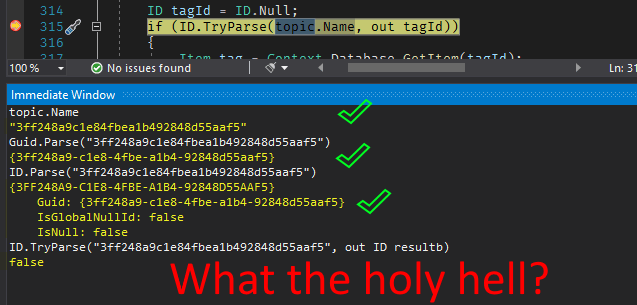
Okay, to go with my LastLoginDate frustrations, I also noticed that when I opened up a User’s Information tab, it always showed the current date and time. Even when I know that user is not in use. E.g.:

This is a test user, and hasn’t been used in the last few days. So, what gives?
Continue reading “Sitecore LastActivityDate is updated by the act of trying to view it.”